Closely related to relocation is protection which is needed to prevent accidents or malicious interference, such as when a program overwrites memory belonging to another program. Surprisingly, a user program can never harm a program "downwind" of it, that is, any program whose base address is lower than its own base address, because that would require negative addresses, and all addresses are interpreted as unsigned, binary numbers.
Several different protection schemes exist. IBM mainframes use key-controlled memory protection. Each user program is assigned a key, which is a small unsigned binary number, usually 4-bits long. Main memory is divided into sections called banks which are equal sized, such as 4 Kilobytes long. A user program is allocated as many of these banks as were needed to store its instructions and data. When an address is generated by an instruction, the key is sent to the memory system along with the address and the memory compares that key value with the key associated with the desired bank of memory hardware. If they are different, an error is signaled. A key value of 0 is reserved for the operating system, which is allowed to tamper with any part of memory.
Fig. 11.5.1 shows a system in operation with four jobs and the operating system.
One drawback of this method is that the size of the key determines how many jobs could be simultaneously active. Four bits means that there could be a maximum of 15 user jobs at any one time, since 0000 is reserved for the operating system. An advantage of this method is that the memory for a user program did not have to be allocated contiguously, i.e. in one long unbroken chunk. It could be spread around the memory. Later virtual memory systems have the same flexibility to break up memory as they need.
Another method, used on CDC mainframes and some micros, can only be used if memory for a job is allocated contiguously as shown in Fig. 11.2.1 (and again in Fig. 11.5.2 below). Another register, the field length register, exists to compare the memory address generated by a program with the maximum address that this program can reach. If the generated address is less than, all is well. Otherwise, the program is trying to reach beyond the end of its memory and an error is signaled. Programs that suffer these errors are halted by the hardware and punished by the operating system.
Fig. 11.5.2 shows the combination of base address register and field length register. The base address register contains an actual memory address, but the field length register contains the maximum length of the program's memory region in words. For Job A, this would be 1100 since Job A starts at (real) address 2500 and ends at 3599, which is 1100 words.
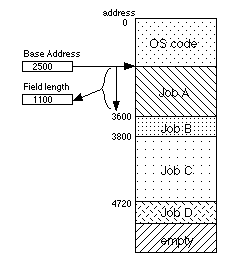
Fig. 11.5.2: Base address register for relocation; Field length register for protection
Every logical memory address that Job A generates while executing instructions is added to the base address and the new value is copied into the real MAR. At the same time, that logical address is compared to the value in the field length register, and if the result is negative, a memory protection error is signaled and the memory operation never completes. Further, Job A is halted in its tracks and a nasty error message is printed out by the operating system.
Comparison is usually done by subtraction. In this system the sign of the outcome determines if the field length value is less than or greater than the logical address.
Fig. 11.5.3 shows this two-way manipulation of the logical address, which happens at the same time and uses extra hardware for speed. The main adder of the ALU is not used to do this address translation.
In Fig. 11.5.3, an illegal out-of-bounds address is generated, which causes the program to halt. The logical address, 1205, is larger than the field length, which is only 1100 words. Though the physical address 3705 is generated (1205+2500), it is never allowed to get to memory because the error halts everything until the operating system can clean up after the offending program.
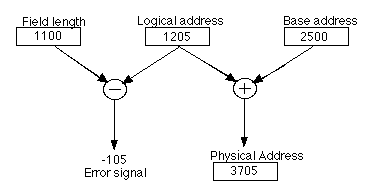
Fig. 11.5.3: Translation of logical address and checking for memory protection violation